I recently open sourced a simple Micropython library for LoRaWAN on the Raspberry Pi Pico. (If you are interested, You can find it on GitHub.) If you are unsure what that all means, let me unpack it for you...
Micropython is a slimmed down version of Python 3.x that works on microcontrollers like the Raspberry Pi Pico, and a host of other microcontroller boards.
LoRaWAN is a wireless communication standard that is ideal for long range, low power & low band width data transmission. Its based on a clever technique for making signals work well over distance, called LoRa.
The library I've shared is a wrapper around the existing LoRaWAN support provided by the RAK Wireless 4200 board. The RAK4200 (affiliate link) essentially provides a modem, that can establish a connection to the network and relay messages. It uses the traditional AT command syntax (used by the modems of yore!)
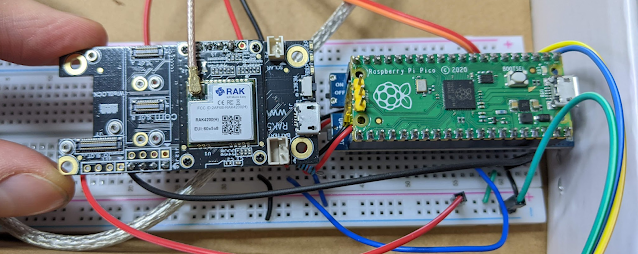 |
| The Pico and RAK4200 Evaluation board (there is also a UPS under the Pico there - that's optional) |
The library pylorawan provides a convenient way to use/control the device directly from your Micropython code. You can just provide the keys to the network, device etc and the code will handle the connection and retries etc. This is the simplest example, where we just connect and send a couple of hex bytes.
My examples, included in the repo, show connections to The Things Network, a network of LoRa gateways that can receive, process and forward your data. If you live in a rural area (Like me) you might need your own LoRaWAN gateway to use this but, if you live in an urban area you will likely have a LoRaWAN gateway within range esp. in central and northern Europe. There is a map on the TTN website.
The Things Stack Community access has free access for devlopment projects and once configured, your 'app' will receive data send into the network from the gateways.
 |
| The Things Network (TTN) Receiving data (The Hex: AA BB CC DD) from the device. |
I'll hopefully expand on this in the coming weeks.

Comments
Post a Comment